Are we at the dawn of Quantum E-commerce?
Could the Quantum Internet mitigate online security risks with a demonstration of 1-second Quantum transactions?
Recent Research from Chinese scientists suggests in a recent demonstration that Quantum E-commerce may pave the way for secure transactions online. Much of the world depends on the internet for transactions which include everything from banking to commerce. However, security experts have often railed against the security of the current system from different attack vectors that range from quantum computing to brute force attacks. Researchers from China have created an entire quantum e-commerce scheme that is thought to be resistant to attacks.
Quantum E-Commerce Quick Start Guide
E-Commerce to Quantum E-Commerce?
Public Key Cryptography
RSA: Current Cryptography
Quantum Resistant Cryptography
Quantum E-Commerce Internet
QDS
OTUH
References
Quantum E-Commerce Glossary
QKD
QDS
RSA
MDI-QKD
Shor's Algorithm
NIST
Public Key Cryptography
OTUH
E-Commerce to Quantum E-Commerce?
Very few of us need any introduction to the world of e-commerce which has transformed our lives since the development of the Internet and the World Wide Web. We now take for granted the plethora of services that are available at the touch of a button, whether on our smartphones laptops, or a variety of connected devices. Connectivity has exploded with more and more devices being connected, so finding ways that we can all transact online more safely makes perfect sense.
Public Key Cryptography
Modern Internet security schemas rely on public key cryptography. Fundamentally it puts the entire security of modern life at risk from being able to factorise a very large number in a reasonable period. That means given enough computational fire-power secure transations are at risk. No doubt you'll have heard of the problems facing many current security schemas, because if a machine can be built that can uncover those numerical factors then secure transactions are history!
That machine exists, it's a quantum computer, coupled with a quantum algorithm named: "Shor's Algorithm", developed by Peter Shor from MIT. The algorithm allows a sufficiently large quantum computer to quickly crunch through and find those factors in a time that is exponentially faster than classical techniques. The algorithm is well known and well understood by complexity theorists such as Scott Aaronson who work on mathematic proofs to prove whether (quantum) algorithms can offer a quantum advantage over classical techniques.
RSA: Current Cryptography
However, the numbers used in public key cryptographic schemes are huge. A typical RSA (Ron Rivest, Adi Shamir, and Leonard Adleman) scheme can use hundreds or thousands of bits while the latter schemes offer 4096 bits which means that currently it is thought beyond being compromised by a quantum computer. RSA developers Ron Rivest, Adi Shamir, and Leonard Adleman, whose last names form the RSA acronym, developed a solution after a year or so of working on the problem.
Quantum computers can factorise a small number currently and a really small number and it takes even longer than you and I can do in our head. So it is thought that whilst there is no immediate threat when quantum computers become more powerful, larger numbers can be factored with ease. There was much speculation in 2023 when an article was released suggesting that RSA-2048 has been broken without even a quantum computer. That article however was not recreated and turned out to be unrepeateable.

Quantum Resistant Cryptography
As you'd expect, with so much at stake and the entire modern world dependent on commerce online, quantum-safe schemes are being developed that claim to offer defense from attacks from the likes of Shor's algorithm and a quantum computer. The field is growing and developing and requires much longer to do this field justice. There are proposed schemes out there that are thought to be quantum-resistant and are being pioneered by various groups, researchers, and bodies.
The NIST organization back in 2022 proposed four schemas that are thought to be Four Quantum-Resistant Cryptographic Algorithms. Of course, time will tell whether the proposed schemes are as secure as thought and that is the great aspect of the security community which aims to make standards open to allow academics, researchers, and anyone to "kick the tires" and test for vulnerabilities.
Quantum E-Commerce Internet
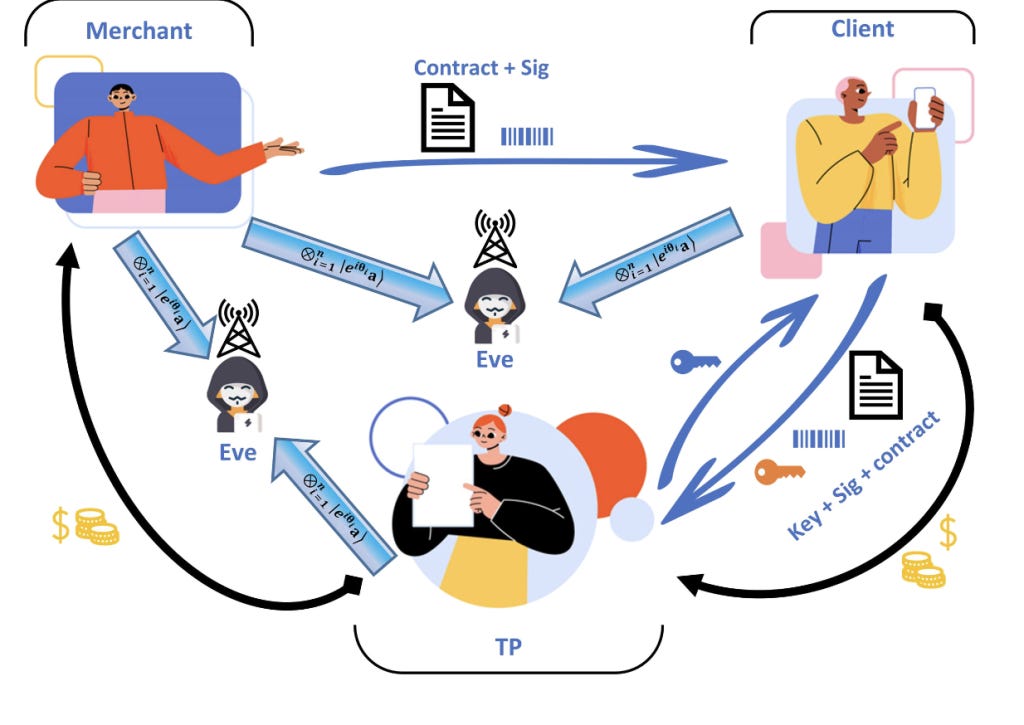
The researchers report on their research which improves on existing schemes. The key innovation is the ability to sign multibit documents with high efficiency while mitigating the impact of imperfect devices. That means that in the noisy world of connectivity (which is the modern internet), and typical of every system, the schema can cope with demands placed on it for completing secure transactions.
QDS
Quantum Digital Signatures (QDS) are one technology that has historically been suggested for information-theoretic security and is suitable for e-commerce-type scenarios. QDS is a technology that has been around for over 20 years but is considered impractical for most real-world scenarios.
OTUH
The new scheme is inspired by the OTUH (One Time Universal Hashing) scheme and four-phase MDI-QKD Measurement Device Independent Quantum Key Distribution. According to the article, the scheme can sign multi-bit documents which means that there should at least be fewer performance limitations. Typical schemes are often inefficient when it comes to multibit cases, and their performances are far from classical solutions.
In terms of performance, The QDS scheme can complete multiple contract signatures within 1 second, narrowing the gap between quantum and classical schemes, which could be acceptable for typical commerce scenarios that we encounter today.
The demonstrated setup of the Quantum E-Commerce recreated a real-world scenario where the Merchant and Client need to carry out a transaction and establish a consensus to complete it. A Third Party is introduced to finish the process of the transaction. The researchers do not automatically assume that the third party is trusted and therefore this makes for a better use case. The size of the message is 428072 bits, with that document being the Amazon Web Services Customer Agreement (perhaps not the most exciting document!).
References
The work on Quantum E-Commerce was Published in Science on the 12th Jan 2024, the authors are Xiao-Yu Cao, Bing-Hong Li, Yang Wang, Yao Fu, Hua-Lei Yin, Zeng-Bing Chen.
Quantum E-Commerce Glossary
QKD
Quantum Key Distribution (QKD) is a method used in cryptography to securely share encryption keys between two parties. The uniqueness of QKD lies in its foundation on the principles of quantum mechanics, which ensures a high level of security.
QDS
Quantum Digital Signatures (QDS) are a quantum analogue of classical digital signatures, used in cryptographic protocols to ensure the authenticity and integrity of a message. Unlike classical digital signatures, QDS leverages the principles of quantum mechanics, offering potentially higher security guarantees.
RSA
RSA, named after its inventors Ron Rivest, Adi Shamir, and Leonard Adleman, is a widely-used algorithm for secure data transmission. Introduced in 1977, RSA is a cornerstone of public-key cryptography, which enables secure communication in an open digital environment.
MDI-QKD
Measurement-Device-Independent Quantum Key Distribution (MDI-QKD) is an advanced approach in the field of quantum cryptography. It was proposed to overcome specific vulnerabilities associated with conventional Quantum Key Distribution (QKD) systems.
Shor's Algorithm
Shor's Algorithm, developed by mathematician Peter Shor in 1994, is a quantum algorithm famous for its ability to efficiently factorize large numbers and compute discrete logarithms. This algorithm marked a significant milestone in quantum computing due to its implications for cryptography, particularly its potential to break widely used cryptographic systems like RSA.
NIST
The National Institute of Standards and Technology (NIST) is a non-regulatory federal agency within the U.S. Department of Commerce. Established in 1901 as the National Bureau of Standards and later renamed in 1988, NIST's primary mission is to promote innovation and industrial competitiveness by advancing measurement science, standards, and technology in ways that enhance economic security and improve the quality of life.
Public Key Cryptography
Public Key Cryptography, also known as asymmetric cryptography, is a fundamental concept in the field of cryptography. It involves the use of two distinct but mathematically related keys — a public key, which is shared openly, and a private key, which is kept secret. This cryptographic method enables secure communication and data exchange over insecure channels, such as the internet.
OTUH
One-Time Universal Hashing (OTUH) refers to a cryptographic concept involving hash functions. It's a variant of universal hashing, tailored for cryptographic applications, particularly in scenarios where a hash function is used only once.




